Table of Contents
Toggle1. Intro
IICS, short for Informatica Intelligent Cloud Services, also known as Informatica Cloud, is a cutting-edge iPaaS (Integration Platform as a Service) solution provided by Informatica. It facilitates seamless data exchange between various on-premise and cloud-based applications, either within a single organization or across multiple organizations.
Before delving into the IICS Architecture, let’s thoroughly explore each component within the architecture.
2. Informatica Cloud serves as an iPaaS (Integration Platform as a Service) solution.
Informatica Cloud meets the fundamental requirements of iPaaS-based applications, which include:
- You can access it from any device with an internet connection and a web browser application. When you log in to the IICS application, your browser securely connects to Informatica Cloud Services via HTTPS.
- A unified platform featuring multiple wizards that help you construct and test your integration tasks.
- Enterprise orchestration of built processes.
- Centralized monitoring capabilities enable tracking the progress and outcomes of jobs.
- Preconfigured integration templates cater to various recurring business use cases.
- Services for both real-time data integration and bulk data integration are provided.
- Informatica Cloud offers connectors for linking to external data sources and a Connector SDK for developing custom connectors.
3. Informatica IICS Cloud Services
Informatica Intelligent Cloud Services provides a suite of cloud-native services that empower organizations to conduct cloud-native data integration, application and API integration, and data management across private, public, hybrid, or multi-cloud environments.
The services available to you depend on your organization’s license.
Administrator
- Set up users, user groups, and assign roles.
- Define runtime environments.
- Establish connections for sources and targets.
- Utilize add-on connectors for cloud connections.
- Configure schedules for running integration tasks.
Data Integration
- Create batch jobs using a variety of tasks such as Mapping, Synchronization, Replication, and Taskflows.
- Execute tasks on demand, on schedule, and in response to real-time events.
- Import and export IICS tasks for ease of management and collaboration.
Monitor
- Enables monitoring of tasks and taskflows.
- Provides access to session logs, job status, and error logs for monitoring purposes.
- Allows users to stop or restart a job as needed.
Discovery IQ
- Offers a comprehensive view of product usage and activity.
- Provides contextual recommendations and best practices.
Application Integration
- Enables real-time web service-based integration of processes, applications, and systems.
- Facilitates the design, integration, and implementation of business processes across various cloud and on-premise applications.
Application Integration Console
Delivers monitoring and management capabilities for Application Integration.
API Portal
- Oversees the management of APIs for services and processes constructed in Informatica CAI.
- Seamless integration with Informatica CAI.
- Access to API descriptions and metadata.
- Policy management.
- API analytics.
API Manager
- Offers users secure access to the created APIs.
- Empowers users to engage with managed APIs and observe API usage analytics.
4. Informatica Cloud Repository
Informatica Cloud Services encompasses the IICS repository, which stores diverse information regarding tasks. As you create, schedule, and execute tasks, all metadata information is recorded in the IICS repository.
The various types of information stored in the IICS repository include:
- Source/Target Metadata: Metadata of source and target objects, including field names, data types, precision, scale, and any other relevant information, is stored in the IICS repository.
- Mappings: The metadata of mappings and their associated transformation rules is stored in the IICS repository.
- Connections: The repository securely stores connection information, allowing you to connect to specific source and target systems in encrypted format.
- Schedule: The repository retains the schedule details of the tasks configured in IICS.
- Logging and Monitoring Information: The IICS repository stores the status of all jobs triggered within the organization.
The IICS repository is fully managed by Informatica, unlike on-premise tools like Powercenter where users maintain the repository themselves. Therefore, users do not have direct access to the metadata stored in the Informatica repository.
5. Informatica Cloud Secure Agent
The Informatica Cloud Secure Agent is a lightweight, self-upgrading program designed to operate on servers within your network. It is compatible with both Windows and Linux servers.
- The Secure Agent enables you to access all your local resources, including databases, files, and applications, located behind your company’s firewall.
- The Secure Agent securely facilitates communication between the Informatica Cloud Repository, other cloud-based applications, and your local resources.
- The Informatica Cloud Secure Agent serves as the local agent on your server, executing tasks and managing the movement of data from source to target.
- Throughout this process, your source application data never passes through or gets staged on Informatica Cloud servers. It stays securely behind your company’s firewall, ensuring its integrity and privacy.
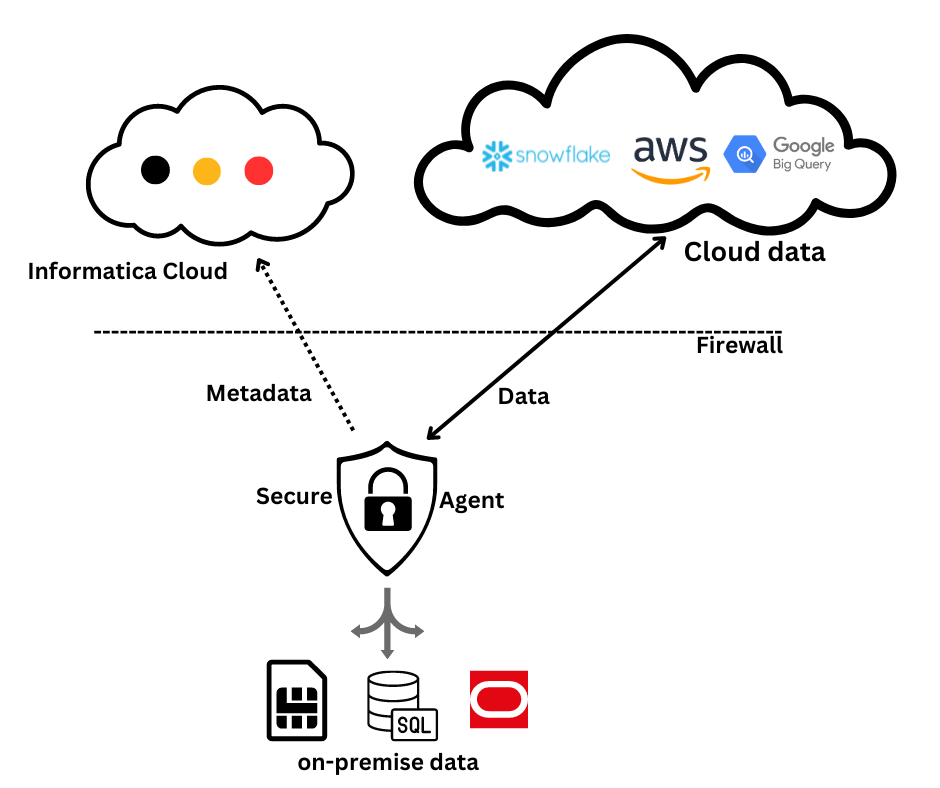
When installing the Secure Agent on your server, you must register it with the Informatica Cloud repository using the unique registration code provided for your organization’s account. Only one agent can be installed per machine. Upon registration of a secure agent, a Runtime Environment is generated within your IICS Organization.
However, you can install the same agent on multiple machines within your network, such as on both a Windows and a Linux machine, and register them with the IICS repository. Each agent can only access the resources available on its installed machine, and you must use the specific Runtime Environment in tasks you build to access them.
Each additional agent typically incurs an additional license fee.
6. Informatica IICS Cloud Architecture
All the components we’ve discussed thus far collectively form the Informatica Cloud Architecture.
- Informatica IICS Cloud as an iPaaS solution.
- Informatica IICS Cloud Services.
- Informatica IICS Cloud Repository.
- Informatica IICS Cloud Secure Agent.

Let’s proceed with a step-by-step examination to understand the function of each component in the IICS Architecture.
- You initiate access to Informatica cloud services through a browser for design and administrative tasks.
- During the design phase, as you begin crafting mappings, Informatica cloud services establish communication with your real data sources, whether they’re located on-premise or in the cloud, through a Secure Agent.
- The source and target metadata, including table names, fields, and data types, are relayed back to the web browser through Informatica Cloud servers.
- Upon saving the design, the metadata is stored in the Informatica Cloud repository.
- When you execute the task, the Secure Agent retrieves the task metadata XML from the IICS repository and brings it into the Secure Agent machine. It then parses the XML data and proceeds to establish connections to your data sources, initiating the data processing.
- The Secure Agent extracts the metadata XML file into the following location on your Secure Agent-installed machine: `<Informatica Cloud Secure Agent installed Directory>\apps\Data_Integration_Server\data\metadata`.
- After completing the data processing through the IICS task, the Secure Agent sends the statistics back to the Informatica Cloud repository.
- End users can access these statistics through the Monitor via a web browser.
Aside from data preview, Informatica only accesses your metadata. Your actual data always remains behind your company firewall at all times.
FAQ's
Informatica IICS architecture consists of several key components, including the Cloud Data Integration Service, Cloud Application Integration Service, Cloud Integration Hub, and Cloud Data Quality Service. These services work together to provide data integration, application integration, data quality, and other capabilities in a cloud-native environment.
Informatica IICS leverages Secure Agents to facilitate data integration between on-premise and cloud applications. These Secure Agents can be installed within your network to securely communicate with both on-premise and cloud-based data sources, ensuring data privacy and security.
The Informatica Cloud Repository serves as a centralized storage location for metadata, schedules, and other configuration information related to tasks and workflows in IICS. It ensures consistency and reliability across the platform.
Yes, Informatica IICS supports real-time data integration tasks in addition to batch-based integration. It allows users to design and execute workflows that respond to real-time events and data changes, enabling timely data processing and decision-making.
Informatica IICS provides monitoring and management capabilities through its web-based user interface. Users can track the status of tasks, view logs, and manage schedules directly from the IICS console. Additionally, alerts and notifications can be configured to notify users of any issues or failures.
Informatica IICS does not impose a strict limit on the number of Secure Agents that can be deployed. However, the number of Secure Agents required depends on factors such as the volume of data, the complexity of integration tasks, and the network architecture of the organization.
Informatica IICS adheres to industry-leading security standards and protocols to ensure data security and compliance. This includes encryption of data in transit and at rest, role-based access control, and compliance with regulations such as GDPR and HIPAA.