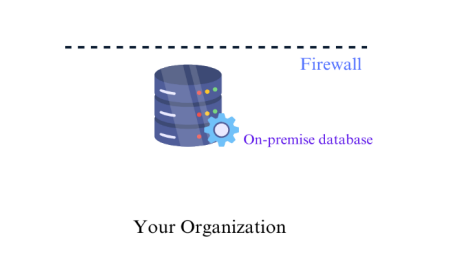
Imagine you possess a customer database housed within your organization’s firewall.
You’re aiming to transfer the data from your customer database to a cloud-based application such as Salesforce, leveraging Informatica Cloud Data Integration.
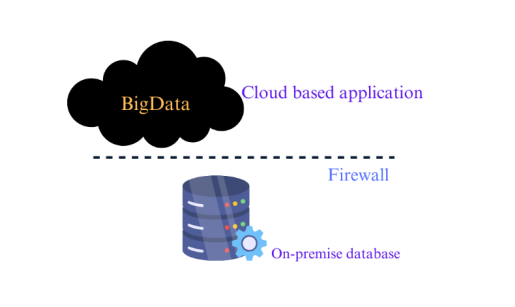
You’ve set up connections to both the source and target applications in Informatica Cloud and created a task to load the data. However, all the metadata, mappings, connections, and logging information for both the source and target are stored in the Informatica Cloud Repository, which is located outside your organization’s firewall.
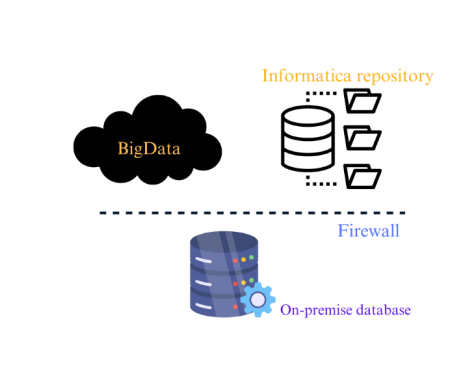
In IICS, the repository is entirely managed by Informatica, unlike on-premise tools like Powercenter where users maintain the repository themselves. Consequently, users don’t have direct access to the metadata stored in the Informatica repository.
Table of Contents
ToggleHow can you securely retrieve the metadata of your organization from the IICS repository and execute the jobs within your company's firewall?
This is where the Secure Agent comes into play.
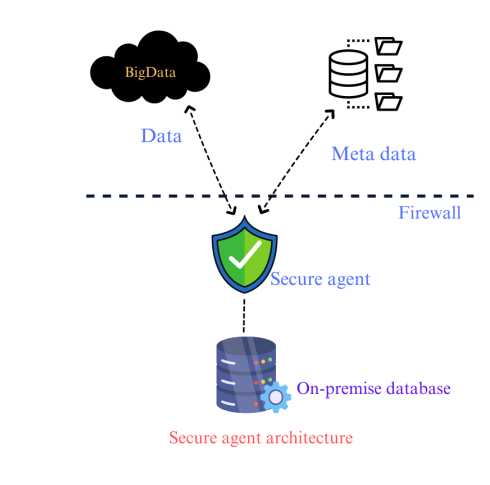
What does the Informatica Cloud Secure Agent entail?
The Informatica Cloud Secure Agent is a lightweight, self-upgrading application that you install on your server and link with the Informatica Cloud repository using a unique registration code provided for your organization’s account. It manages all tasks and facilitates secure communication across the firewall, connecting your organization with Informatica Intelligent Cloud Services.
Accessing metadata from your organization’s IICS Repository, utilizing data from local resources, and executing tasks won’t be possible without registering the Secure Agent.
What are the roles of the Informatica Cloud Secure Agent?
- The Secure Agent ensures secure communication between the Informatica Cloud Repository, other cloud-based applications, and your local resources.
- The Secure Agent functions as a local agent on your server, executing all tasks and managing the movement of data from source to target.
- The Secure Agent enables access to all your local resources, including databases, files, and applications, located alongside your company’s firewall.
- When processing data via the Secure Agent, your source application data doesn’t pass through or run on Informatica Cloud servers. Instead, your data stays securely behind your company’s firewall.
How does the Informatica Cloud Secure Agent operate?
The Secure Agent employs pluggable microservices for data processing. Each service within a Secure Agent is a microservice with its own distinct functionalities and capabilities.
To illustrate, the Data Integration Server is responsible for executing all data integration tasks, whereas the Process Server oversees application integration and process orchestration jobs.
The following image displays the different services accessible within the Secure Agent. The availability of services under a Secure Agent depends on the licenses obtained by your organization.
Microservices are constructed based on an architectural style that enables the development of applications as a set of small autonomous services, each designed to achieve a specific business objective.
- Microservices are designed to be loosely coupled, meaning that modifications made to one service do not impact others.
- Fault isolation is straightforward. Even if one service experiences an outage, others can continue to operate without disruption.
- Additional hardware resources can be allocated to services that are frequently utilized.
- Modifying the data model of one Microservice does not impact other Microservices.
FAQ's
A Secure Agent is a Java program responsible for executing integration tasks and facilitating secure communication across the firewall between our organization and IICS.
To initiate a Secure Agent service:
1. In the Administrator, navigate to Runtime Environments.
2. On the Runtime Environments page, click on the name of the Secure Agent.
3. Select the Details tab.
4. In the Agent Service Start or Stop section, choose the service you wish to start.
5. Click Start.
The Secure Agent machine should have a volume with a minimum of 250GB disk space, and at least 5GB of free space, or three times the size of the Secure Agent installation, whichever is greater. Additionally, the account used to install the Secure Agent must have access to all remote directories containing flat source or target files.
To delete a Secure Agent:
1. In the Administrator, navigate to Runtime Environments.
2. Expand the Actions menu for the Secure Agent.
3. Select Delete Secure Agent. If the Secure Agent is running, a warning message will appear. Stopping an active Secure Agent prevents scheduled tasks associated with the Secure Agent from running.
Port 443 (HTTPS) is utilized by the Secure Agent for internet connections. Ensure that your firewall is configured to permit traffic over port 443. If your POD is USW3, refer to the Knowledge Base article on Informatica Network for details on the IP address ranges that should be added to your list of approved IP addresses for AWS.